If your organization uses Azure Entra to manage employee access to tools and services, you can utilize Azure"Provisioning" feature to automatically provide your users with access to DocuWare via SCIM. This guide will walk you through the steps to configure both DocuWare and Azure Entra to set up provisioning for your organization.
The current version of UserSync (v3) supports the following provisioning features:
Automatic User Creation: Users assigned to the Enterprise application in Azure are automatically created as users in DocuWare.
Attribute Synchronization: Any updates to user attributes (userName, email, activeness) in Azure will be reflected in DocuWare.
User Deactivation: When users are deactivated in Azure, they are marked as 'disabled' in DocuWre, preventing them from logging in.
Creating a new application in Microsoft Azure Entra
Login to the Azure portal via the following link - Home - Microsoft Azure
Go to Enterprise Applications page.
Click New Application:
.png)
Click Create your own application:
.png)
Choose a Name for your app and select the option
Integrate any other application you don’t find in the gallery (Non-gallery):Click Create.
After the creation of the application navigate to Provisioning
Select Provisioning Mode > Automatic.
.png)
Open Admin Credentials section.
Don’t close the Azure configuration and switch to DocuWare Configurations.
Embedding the new Azure application in DocuWare
Go to DocuWare Configuration > Integrations > App Registration.
In the App Registration plugin, select New app registration.
In the Create Application Registration pop-up, choose Web application, then click Continue.
.png)
Enter a Name for the app registration, then:
Select Grant type: Client Credentials
Click Save
.png)
From the just created app registration copy the values of
Application (Client) ID
Client secret
.png)
Switch to DocuWare Configurations > General > User Provisioning.
In the User Provisioning plugin, activate the option Enable User Provisioning.
In the dropdown Identity Provider select Azure Entra.
In the dropdown Application Registration select the previously created app registration - see also step 4.
Click the Save button.
After saving, two authentication methods are provided as options:
OAuth2 Client Credentials Grant and Bearer Authentication..png)
The next steps depend on your authentication method choice:
OAuth2 Client Credentials Grant
Copy the links Tenant URL, Token Endpoint.
Navigate back to Entra > your application > Manage > Provisioning > Admin Credentials.
Make sure that the OAuth2 Client Credentials Grant is selected in the Authentication Method dropdown.
Paste all the copied data from step 5 in the appropriate fields there.
When all the required data is populated click the Test Connection button.
Then Save the changes.
If an error is displayed in the top-right corner after saving, click the Save button again.
.png)
Bearer Authentication
Copy the link for the Tenant URL and the generated Bearer token.
Navigate back to Entra > your application > Manage > Provisioning > Admin Credentials.
Make sure that the Bearer Authentication is selected in the Authentication Method dropdown.
Paste the previously copied link for the Tenant URL and the Bearer token.
When all the required data is populated click on the Test Connection button.
Then Save the changes.
.png)
Mapping user and group attributes in DocuWare and Microsoft Entra ID
Mapping user and group attributes between DocuWare and Microsoft Entra ID allows users and groups to be matched and synchronized
Open Microsoft Entra ID.
To map the users choose Provisioning > Attribute Mapping > Provision Microsoft Entra ID Users
.png)
Set the User attribute mappings:
Required mappings:
userName: Item(Split([userPrincipalName], "@"), 1)
active: Switch([IsSoftDeleted], , "False", "True", "True", "False")
emails[type eq "work"].value: Coalesce([mail],[userPrincipalName])
externalId: objectId
Optional mappings:
name.givenName: givenName
name.familyName: surname
Additional Information
For mapping the userName attribute you will need first to update its configuration:
Open for Edit Attribute the attribute: userPrincipalName
Change the mapping type to Expression
Update the expression field to: Item(Split([userPrincipalName], "@"), 1)
Click OK to save.
.png)
For mapping the email attribute you will need first to update its configuration:
Open for Edit Attribute the attribute: emails[type eq "work"].value
Change the mapping type to Expression
Update the expression field to: Coalesce([mail],[userPrincipalName])
Click OK to save.
.png)
For mapping the externalId attribute properly you will also need to first update it’s configuration:
Open for Edit the attribute: externalId: mailNickname
Change the Source attribute to: objectId
Click OK to save.
.png)
Delete all the extra mappings and Save. If the mappings are not deleted, it can cause errors when updated users are provisioned.
.png)
To map the groups choose Provisioning > Attribute Mapping > Provision Microsoft Entra ID Groups
.png)
Set the Groups Mappings:
Delete the redundant mapping externalId → objectId
Disable the Delete option from Target Object Actions
Save the changes
.png)
Provisioning users and groups
Navigate to the Overview page in your Entra application and click the Start Provisioning button:
.png)
Provisioning users
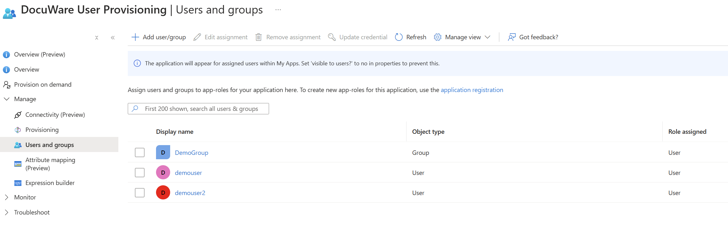
Click Manage > Users and Groups > Add user/group > Select the users you would like to provision > Assign.
After adding the desired users for provisioning, they will either be automatically provisioned after some time or you can choose to provision them on demand.
.png)
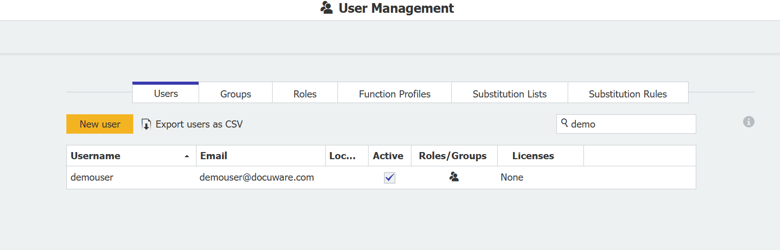
Navigate to DocuWare Configurations > General > User Management.
Check if the expected users are provisioned successfully there.
Provisioning groups:
Click Manage > Users and Groups > Add user/group > Select a group for provisioning > Assign.
Note: If you want to assign the members of the group on-demand, you must add them to the list as well.After adding the desired groups and users for provisioning, they will either be automatically provisioned after some time or you can choose to provision them on demand.
Navigate to DocuWare Configurations > General > User Management.
Check if the expected groups and users are provisioned successfully there.
.png)
Additional information about Group Provisioning Process :
Searching for Groups: The system first searches for an existing group using the given displayName. If a group with that displayName exists in DocuWare, the process moves to updating the group; otherwise, it proceeds to creating a new group.
Group Creation and Update Handling:
a) Creating New Groups: When no existing group in DocuWare matches the displayName, the service creates a new group with the specified members.
b) Updating Existing Groups: If a matching group is found, the service updates the group’s details and adds new members to the group. It ensures that existing members are not replaced but retained alongside the new members.Once the groups are mapped after their first synchronization, future mapping is done using the ID attribute. For example, if you decide to change a group's name in Entra ID and then provision the updated group, the group will be mapped by its ID. The service will update the group's name in DocuWare accordingly without removing its members.
Member Management:
a) Adding Members: When updating groups, any new members are added while keeping the current members intact.
b) Preventing Duplicates: The system is designed to avoid adding duplicate members to groups, ensuring each member is unique within the group.