To access your DocuWare system externally, for example via the Internet, you should note of the following points. This also applies if you want to use public forms with DocuWare Forms.
Required ports: If you set up external access to your DocuWare system, only the ports of the Web Client (by default port 80 or 443) need to be approved in the firewall of your DocuWare system. More information about ports can also be found in the "Server-Server Communication" matrix in the "Communication Technologies" chapter.
HTTPS (TLS/SSL): The DocuWare Web Client and the DocuWare Desktop Apps support all current HTTPS. To configure the DocuWare Web components for HTTPS (TLS/SSL), you must carry out the following steps in IIS manager:
Import the certificate or certificates ("server certificate", "Import" action)
Adapt the website link and make it accessible via TLS
Remove the HTTP link for security reasons
If you use a self-signed certificate, you must also ensure that your certification center is defined as a trusted certification center on all clients. To do so, import the certificate into the certificate store of all computer and user accounts in your domain, for example using a Group Policy Object (GPO) from Microsoft.
Split DNS: To be able to use the Identity Service of DocuWare, you must have set up Split DNS. This is the only way to resolve the host name to an IP address in the internal network and another IP address in the external network and to avoid certificate error messages.
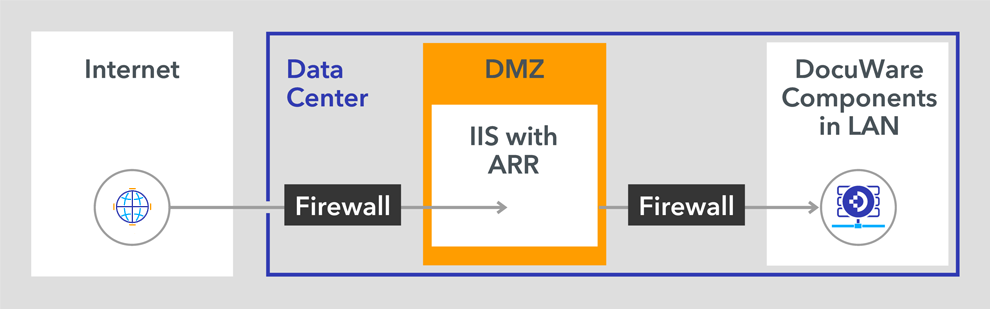
Demilitarized Zone (DMZ): The DocuWare Web components connect directly with the database. It is therefore not recommended to install the DocuWare Platform Service in a DMZ, for example. All components, including the Web components, should only be installed within the LAN. The Web Server in the DMZ should route requests accordingly to the internal Web Server, for example, using Application Request Routing (ARR). More information about ARR can be found in the Load Balancing section of the DocuWare Server Setup.
Protecting sensitive data outside of DocuWare: Some of the data of DocuWare is unshielded and cannot be protected by specific DocuWare security mechanisms. This include the index data of the documents and the extracted full text, which are stored in their respective databases. Every system administrator with sufficient privileges to view the database can access these data. Fulltext is also stored in a separate index that is controlled by the fulltext server. The fulltext server is based on Apache SolR, a widely used fulltext engine.
If these data repositories contain sensitive data, then access to the databases, to the index location, and the access to the full text server URL - by default http://machinename:9012/solrt need to be restricted by the administrator using common methods such as access control lists for file directories or databases as well as a transparent Encrypted File System (EFS) for the fulltext user.