When you add an electronic signature to a document, the process involves more than just adding a signature at the bottom of a text. Most of the steps take place behind the scenes, controlled by software.
In simple terms, every form of electronic signature consists of data that is added to a document or file. With the qualified electronic signature, this added data is generated by hardware security modules (HSM) in a particularly secure technical environment. In regions with a tiered system of legal regulation for signatures as a trust service, such as in the EU, a specially authorized and qualified body has also issued the signatory's authenticated proof of identity, the digital certificate.
Signing takes place in what is known as a public key infrastructure, in which an encryption procedure with two software keys is used. One is the private one, which only the encrypting authority knows, and one is the public one. The latter is provided along with the document in the signature certificate for the recipient.
There are three steps in the process:
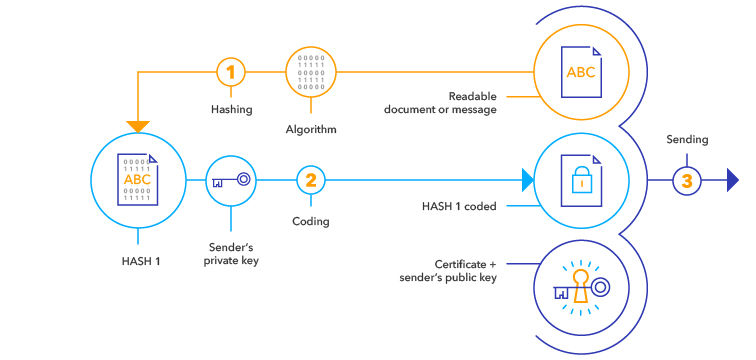
Calculating the hash value
A mathematical function is used to calculate a checksum from the data of the document or file, which is called a hash value. This is like the document's fingerprint.Encrypting the hash value
This hash value is encrypted with the signer's private key.Connecting the encrypted hash value + certificate with the document
The encrypted hash value and the certificate are attached to the document. The certificate contains the public key to decrypt the hash value, the information that this key is associated with the identity of the signer, and the validity of the certificate.